THE HIDDEN CERTIFICATES IN YOUR ORGANIZATION HOW TO FIND THEM

It should be clear by now why centralizing visibility over your cryptographic assets is essential to digital trust. If for some reason you’re unmoved by the parade of damaging outages and data breaches caused by expired or improperly secured TLS certificates over the last several years, consider the number of certificates that the average enterprise has to manage. According to a 2021 DigiCert survey, the average enterprise estimates they have an average of 50,000 server certificates to manage.
This already high number doesn’t include all the user and device certificates that the average enterprise needs in addition to these server certificates. Nor does it account for the growing number of digital certificate use cases and the accompanying exponential increase in TLS certificates overall.
And certificates are stashed everywhere in your IT environment. Here’s an incomplete list of where you might find them:
-
Public certificate authorities (CAs), including DigiCert
-
Private on-premise CAs, most commonly Microsoft CAs, which are often stood up without oversight
-
Private cloud CAs like AWS Private CA
-
Web servers like Microsoft IIS and Apache
-
Load balancers, including F5, Citrix, A10 and AWS Elastic Load Balancer
-
Vulnerability scanning tools, such as Qualys and Tenable
-
Cloud native Kubernetes clusters
Nearly half of the enterprises surveyed have discovered so-called “rogue” certificates deployed without IT’s knowledge—certificates that are currently unmanaged. Chances are that you have tens of thousands of certificates lurking across your organization that you don’t know about.
That’s why it’s essential that your organization maintains a complete, continuously updated inventory of all your certificates. To achieve this, you need the capability to discover every one of these certificates no matter how they’re used, who owns them or where they’re located.
It isn’t enough for a certificate lifecycle management (CLM) solution to simply assert that it can discover certificates. An effective CLM solution must also provide multiple mechanisms to discover them—because frankly, there’s no one way to perform this crucial task.
What are some of the ways an effective CLM solution should be able to discover certificates? Let’s take a look.
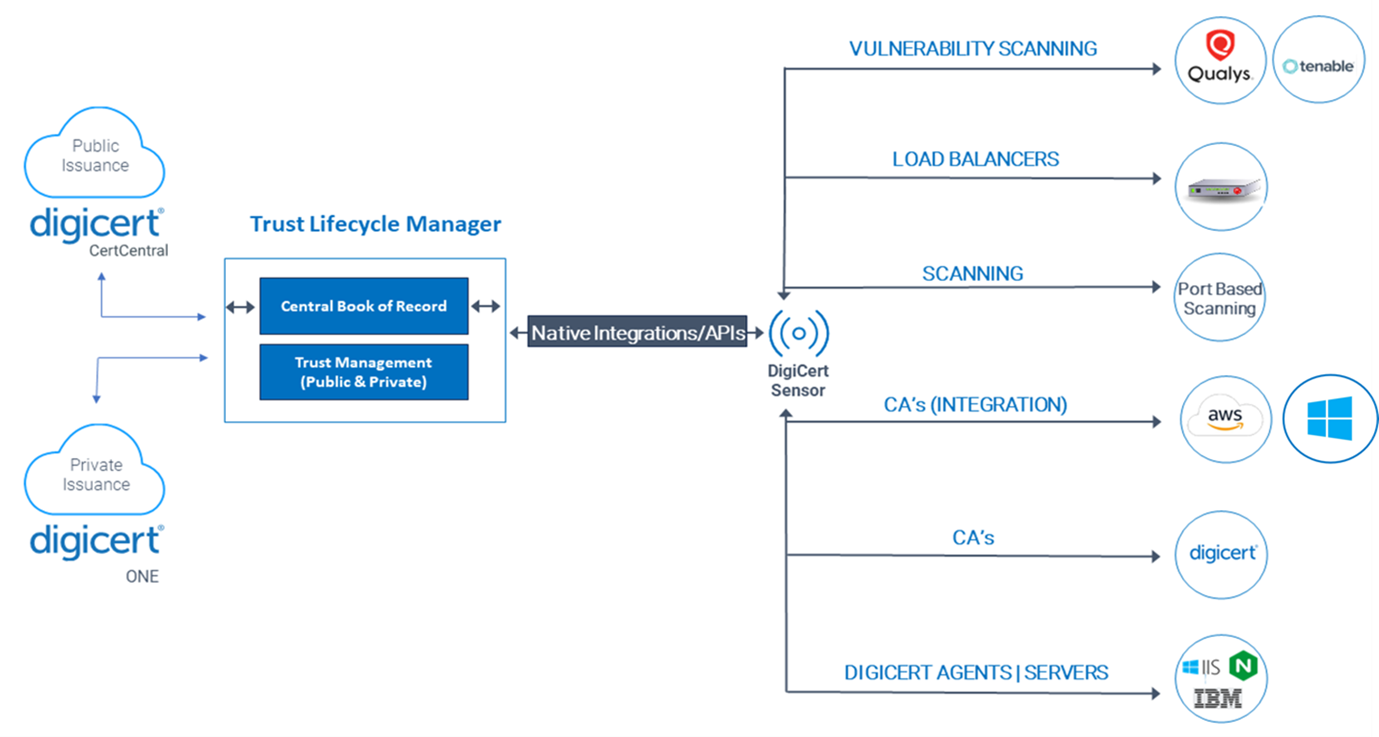
Integration with CertCentral and DigiCert® ONE CA Manager
At first glance, the most obvious way a CLM solution can discover certificates is through tight coupling with the certificate authority (CA) that built the solution. DigiCert® Trust Lifecycle Manager can discover public certificates issued by DigiCert CertCentral® and private certificates issued by DigiCert ONE CA Manager. This integration streamlines certificate lifecycle management from issuance to centralization, enabling you to discover these certificates seamlessly. This full-stack capability is something most CA-agnostic CLM providers can’t provide—something to consider if you’re already a CertCentral customer.
Integrations with third-party CAs
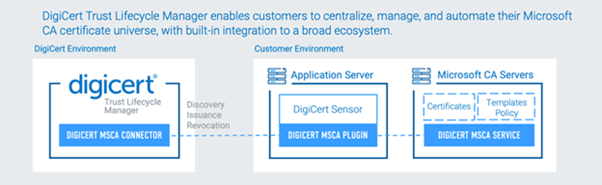
Of course, not every issued certificate comes from DigiCert. It would be hard to find a Global 2000 enterprise that doesn’t have one Microsoft CA (or 20) strewn across their environment. Meanwhile, as more organizations migrate much of their infrastructure to the cloud, many of them are contending with certificates issued from AWS Private CA, among others. That means you need a way to discover certificates issued from these CAs so they can be imported and catalogued in your central certificate inventory.
Most CA-based solutions are unable to discover certificates that don’t originate with them, a selling point that legacy CA-agnostic solutions harp on incessantly. In contrast, DigiCert Trust Lifecycle Manager is at once a CA-centric and CA-agnostic solution—a neat (and supremely useful) integration!
DigiCert Trust Lifecycle Manager does more than simply root out certificates issued by other CAs. Once these third-party certificates are imported into your certificate inventory, you can apply tags that identify these certificates and enable you to apply predefined automations and filtering options.
Port-based scanning
Port-based scanning is the most basic way to discover certificates that don’t come directly from a CA. A CLM solution drops a sensor in your IT environment and does the heavy lifting searching for certificates. You can specify the ports you need scanned or a range of IPs—both on-premise and in the cloud—to identify assets, including active services and certificates associated with an IPV4 address. This scanning ensures that your certificates are secure, properly managed and comply with industry standards. It also ensures their integrity is maintained within your organization’s network infrastructure.
DigiCert Trust Lifecycle Manager can find many certificates using its port-based scanning functionality. But certain certificates, such as those found on load balancers and web servers, require additional help to discover.
Leveraging sensors to find certificates behind load balancers
By itself, port-based scanning can identify open ports and services that are running on a load balancer. But it can’t help you identify the TLS certificates themselves because load balancers terminate TLS connections and then route traffic to backend servers. Because these ports aren’t exposed, you need sensors to monitor network traffic at strategic points within your network and analyze the traffic as it moves through these points. This handshake data can identify the certificates being used on servers that sit behind your load balancers, giving you visibility into them and synchronizing them in your central inventory.
DigiCert Trust Lifecycle Manager can leverage its sensors to automate certificates behind load balancers, which is essential given the high number of certificates typically associated with load balancers. Its infrastructure not only ensures they become part of your complete certificate inventory but also identifies additional certificates that may be living within these already complex environments.
Import from agents
Certain certificates, such as those installed on Microsoft IIS or Apache web servers, are not discoverable using port-based scanning. To discover them, you need to install agents directly on these servers that can gather specific information about these certificates, including their expiration dates and associated domains, and relay that information to your central inventory.
DigiCert Trust Lifecycle Manager supplies these agents to give you the flexibility to discover these certificates when other methods are unable to. In addition, DigiCert Trust Lifecycle Manager’s agents provide the internal authentication you need so that outside sources aren’t touching your servers.
Leverage existing vulnerability detection tools
All the discovery mechanisms we’ve mentioned are necessary when building and maintaining a continuous central certificate inventory. But many organizations, particularly Fortune 500 companies, use vulnerability management solutions like Qualys or Tenable that can detect vulnerabilities on most networked assets—physical and virtual servers, routers and switches, cloud instances, containers and even IoT devices like multifunction printers—and would prefer to leverage this already deployed infrastructure when scanning for digital certificates.
These vulnerability detection solutions are already scanning all corners of the network, building and maintaining a complete inventory and layout of your enterprise environment. Instead of putting a bigger burden on your network and potentially creating more access complexities for SecOps teams, DigiCert Trust Lifecycle Manager lets you piggyback on this existing data and immediately build your complete certificate inventory. This integration also assures a comprehensive record of cryptographic assets in a way the legacy CLM solutions that lack these integrations cannot.
Having all the tools you need to build digital trust
Cryptographic assets like keys and certificates can be found everywhere in your IT environment, from your physical data centers to the cloud. And the process of discovering all of them and building a continuously updated central inventory is an incredibly complex task. Having multiple easily deployable mechanisms of discovery at your organization’s fingertips allows you to have faith that your inventory is comprehensive and actionable.