
Important Update: Changes to TLS Certificate Policy & Client Authentication EKU Removal
What’s Changing in TLS Certificate Policy?
Browser vendors like Google Chrome and Mozilla Firefox are enforcing a major change: after June 15, 2026, public TLS server certificates must not include the Client Authentication Extended Key Usage (EKU). This update, while technical, has far-reaching consequences—especially for financial institutions that rely on certificate-based authentication for secure communications.
What is Extended Key Usage (EKU) and Why is it Changing?
Extended Key Usage (EKU) is a critical field within an X.509 digital certificate that dictates the specific functions for which the certificate's public key can be used. The two most relevant EKUs in this context are:
-
Server Authentication (OID 1.3.6.1.5.5.7.3.1):
This is the standard for SSL/TLS certificates. It verifies the identity of a server to a client (e.g., your browser), enabling secure HTTPS connections.
-
Client Authentication (OID 1.3.6.1.5.5.7.3.2):
This EKU is used to verify the identity of a client to a server. It's a cornerstone of security models like mutual TLS (mTLS), where both parties in a connection must present and validate certificates.
While this overlap was previously tolerated, it is now recognized as a security risk. Including Client Authentication in server certificates can lead to misuse and vulnerabilities, violating the principle of least privilege.
Browsers are now drawing a clear line: Certificates must serve a single purpose. Chrome will reject any server certificate containing the Client Authentication EKU after June 2026, and other browsers are expected to follow.
Why Does This Matter for Financial Services?
Financial institutions often use public TLS certificates for both website security and internal authentication (like mTLS and device identity). This “Swiss Army knife” approach is no longer viable. If you continue using multipurpose certificates, you risk browser distrust and potential outages.
Real-World Example
The images below show a current DigiCert EV certificate for www.jnrmr.com, which includes both server and client authentication EKUs—a configuration that will soon be non-compliant:
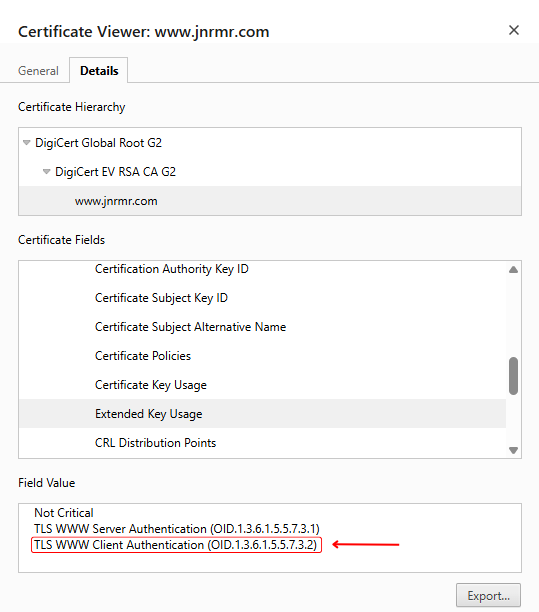
Timeline: What’s Happening and When?
| Date | Change |
|---|---|
| October 1, 2025 | DigiCert stops including Client Authentication EKU by default in public TLS certificates |
| May 1, 2026 | DigiCert fully removes Client Authentication EKU from all new, renewed, and reissued public TLS certificates |
| June 15, 2026 | Chrome and other browsers will distrust certificates with both Server and Client Authentication EKUs |
What Should Organizations Do?
Review Your Certificate Usage
-
Audit all public TLS certificates to identify any used for client authentication.
-
If you only secure websites (HTTPS), no action is required.
Plan Your Migration
-
For mTLS, device identity, or server-to-server authentication, you must transition to alternative solutions before May 2026.
Your Options
| Option | Description |
|---|---|
| DigiCert’s X9 PKI | Purpose-built for finance, X9 PKI supports both server and client authentication, is browser-independent, and ensures strong interoperability and security. Ideal for multi-organization communications. |
| Private PKI Solutions | Managed private PKI for strictly internal use, giving you control and flexibility for internal authentication. |
| Certificate Lifecycle Management | Use tools like DigiCert Trust Lifecycle Manager to inventory, manage, and automate your certificate environment. |
Why Is This Happening?
This crackdown is part of a broader move to eliminate “multipurpose roots”—certificate hierarchies that support both server and client authentication. Google and other browsers see this as a security risk, pushing the industry toward more precise, role-specific PKI architectures.
The Path Forward: Embrace Modern PKI
The removal of ClientAuth from public TLS certificates is more than a compliance update—it’s a turning point. Financial institutions must:
-
Separate public and private trust zones
-
Modernize private PKI for agile use cases
-
Adopt interoperable, policy-aligned certificates like those from X9 PKI
Collaborative efforts like the X9 PKI Industry Forum are guiding financial organizations through this transition, ensuring technical alignment and future-ready frameworks.
Final Thoughts
Certificate hygiene is now foundational to digital trust. Organizations that audit their certificate usage, modernize PKI, and adopt purpose-built trust models will be best positioned for secure, reliable operations in the evolving landscape.